VPNs
Warning
This section is under construction
Danger
There are a lot of old VPN technologies out there that are old and insecure. This section will not cover those technologies.
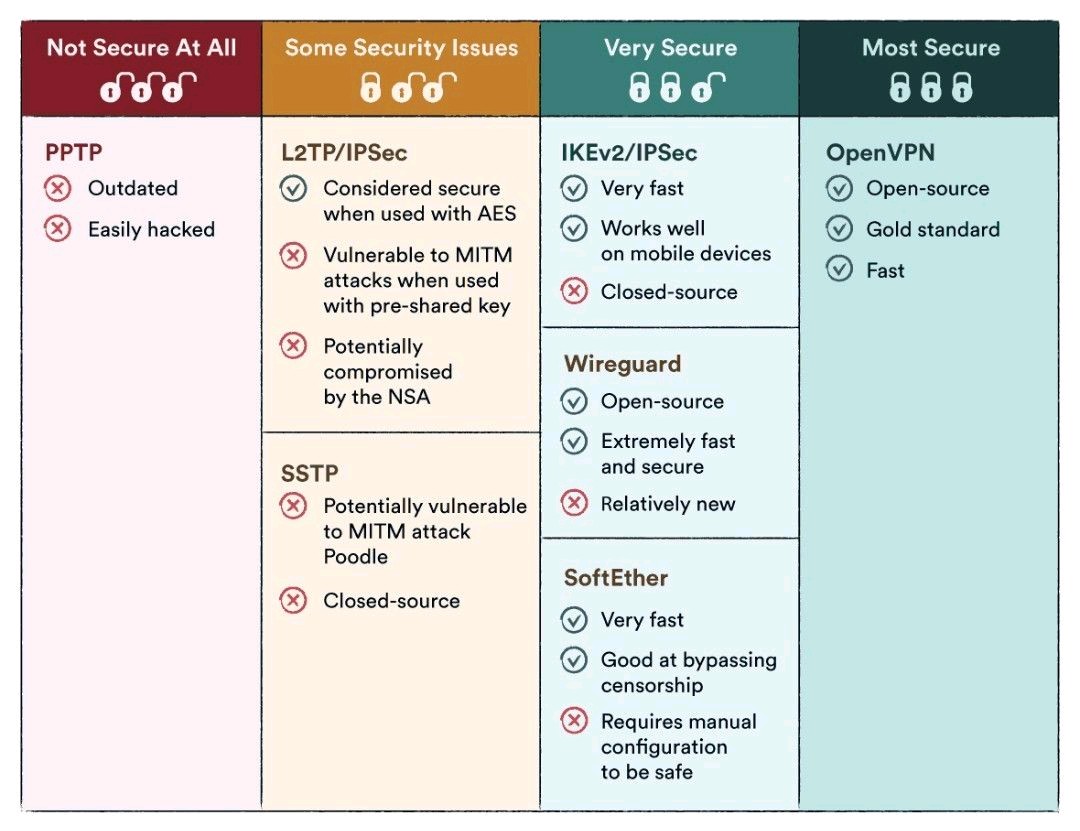
Tip
To improve traditional encrypt-then-MAC VPN solutions, one should choose modern AEAD ciphers like AES-GCM or ChaCha20-poly1305.
OpenVPN
Danger
More research is required on the OpenVPN TLS protocol. Watching a YouTube video for one of my academic courses stated that TLS does not rekey. Prolong connections can be susceptible to cryptanalysis
Tip
While OpenVPN allows either the TCP or UDP protocol to be used as the VPN carrier connection, the UDP protocol will provide better protection against DoS attacks and port scanning than TCP:
IPSec
Cite
WireGuard
WireGuard’s protocol was developed from scratch, based
on best cryptographic practices and using the newest ciphers. Contrary to committee-guided protocols like IPsec, WireGuard is strongly opinionated on certain topics and includes radical ideas. It does away with cryptographic agility by locking in on a single AEAD cipher and authentication algorithm with no feature negotiation: ChaCha20-poly1305. Backwards compatibility is explicitly missing: handshake and key derivation include a hash of the protocol version number, so two different implementations will derive distinct keys, making them permanently non-compatible. These measures heavily incentivize keeping the software up-to-date and prevent degradation attacks found in SSL.
Cite
- Hulsing, A., Ning, K.-C., Schwabe, P., Weber, F., & Zimmermann, P. R. (2021). Post-quantum WireGuard. 2021 IEEE Symposium on Security and Privacy (SP), Security and Privacy (SP), 2021 IEEE Symposium on, SP, 304–321. https://doi-org.ezproxy.snhu.edu/10.1109/SP40001.2021.00030
- Lipp, B., Blanchet, B., & Bhargavan, K. (2019). A Mechanised Cryptographic Proof of the WireGuard Virtual Private Network Protocol. 2019 IEEE European Symposium on Security and Privacy (EuroS&P), Security and Privacy (EuroS&P), 2019 IEEE European Symposium On, 231–246. https://doi-org.ezproxy.snhu.edu/10.1109/EuroSP.2019.00026
- Priambodo, D. F., Amiruddin, & Trianto, N. (2021). Hardening a Work from Home Network with Wireguard and Suricata. 2021 International Conference on Computer Science and Engineering (IC2SE), Computer Science and Engineering (IC2SE), 2021 International Conference On, 1, 1–4. https://doi-org.ezproxy.snhu.edu/10.1109/IC2SE52832.2021.9791983